One of our engineers was working on migrating a customer from a legacy email server into Office 365 after we discovered they were under a brute force external attack.
The migration required that we receive the users passwords. These would, of course, be reset after the migration. It’s an old system and we found that many users didn’t know their passwords.
To overcome this, we had to delve into our toolbox. With the client’s agreement, we decided to run an experiment to see if we could glean any details from a packet capture.
It turned out to be easy. We were able to pull all the usernames and passwords in plain text from the network!
This means it would be relatively straightforward for a potental attacker to completely compromise this organisation.
All they would have to do was park in their carpark afterhours, crack their wifi (an easy task) and capture the login attempts. Ultimately this would result in the loss of all their systems and potentially the whole business.
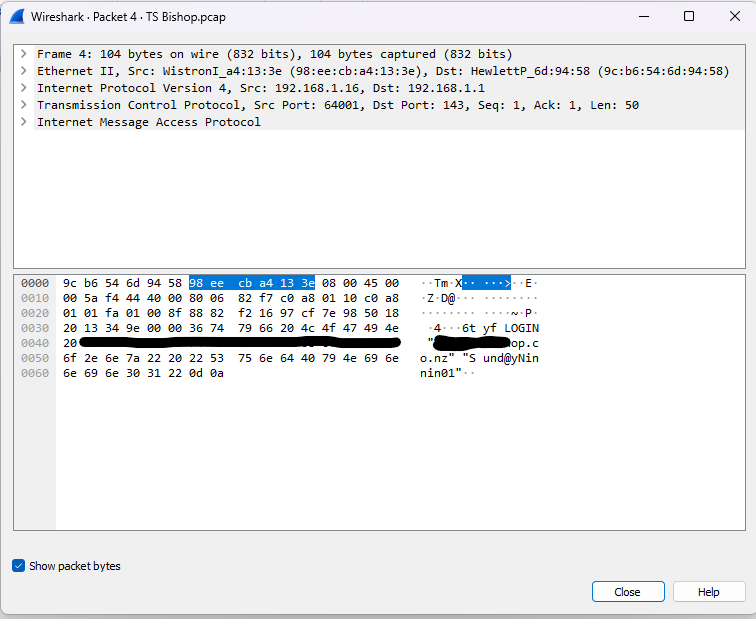
Luckily that risk is eliminated by a move to a secure cloud system with encrypted passwords and MFA.
Thankfully, this client is now taking security seriously and we are migrating them off legacy systems into more secure and up to date cloud services, but this is a great example as to why legacy systems present a risk to businesses.
