What expert cyber-security does my business need?

The inconvenient facts about Cyber Security
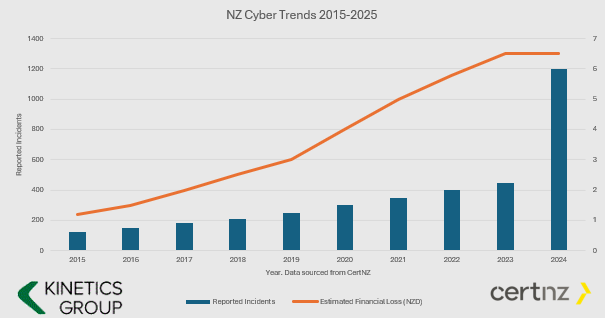
- The number and value of incidents is increasing.
- Cyber Crime is BIG business and they keep investing in new tools.
- If you aren’t keeping your defences up, then it is only a matter of time before you fall victim (i.e. if your cyber protection is the same now as it was even just one year ago, then you are increasingly vulnerable.
- You have to ward them off every hour of every day, they only have to get through once.
You might say this is scare-mongering. If all this hacking is going on and nothing has happened yet, then surely I don’t need to worry?
We’d say “good luck to you – why do you have seat belts in your car? – its only a question of time.”

What Cybersecurity Protection Level Do You Need?
Q: Does this mean I don’t need cyber-insurance? A: You still need cyber-insurance. We can only reduce your risk (and most insurers will want to see these protections in place before they will offer cover)
Q: What is involved installing KARE? A: Once a PC, Mac, Tablet or Phone is ready, our scripts run every time you login and the security tools auto-install – with configuration for corporate devices and BYOD.
AD HOC
STRUCTURED LAYERS based on the CertNZ Critical Controls Framework
For organisations in the cloud with minimal reliance on IT.
Everything is in the cloud. There are only a few PCs/Macs and iPhones/Androids to protect.
For organisations in the cloud, and maybe a small number of servers, looking to be more thorough.
Add in depth reporting, server backup and identity monitoring.
Pick KARE FOUNDATION SME
For organisations that value a structured, proactive and comprehensively protected IT.
Add more scrutiny and awareness, personalised cyber training and business planning.
For organisations in the cloud with minimal reliance on IT
Everything is in the cloud. There are only a few PCs/Macs and iPhones/Androids to protect
For organisations in the cloud, and maybe a small number of servers, looking to be more thorough
Add in depth reporting, server backup and identity monitoring
Pick KARE FOUNDATION SME
For organisations who value a structured, proactive IT engagement
Add more scrutiny and awareness, personalised cyber training and business planning

Enhanced Security Services & Add-Ons
+ Choose additional services as required
Add Fixed Monthly Support Fee
No cost surprises. One fee for all business-hours support
(excludes projects and training)
Add Security Plus
24/7 SOC
IT Assets locked
Only protected devices can access them
Add Managed Firewall
Network firewall
Kinetics supplies and manages on a monthly contract
Add Password Vault
Organisation Wide
Maintain unique, complex passwords for all users and/or shared with teams
Add 365 Cloud Backup
Content backup for 365
Go over and beyond the standard Microsoft backup protection
Backup and Continuity
A range from backup to stand-by services
Because you have servers, you need to back them up

How about the broader cyber-framework?
Comprehensive Data Protection & Compliance
Platform Security is just part of a broader cyber-security and data protection framework.
Have you considered how manage your data within your Microsoft tenancy? How’s your Microsoft “Secure Score“? As you get the external security set up, let us work with you to manage the other side – your internal security.
Our consultants can work with you to understand what data your organisation maintains, and the obligations (and client expectations) and the rules that need to be established to protect it. Who should have access to which libraries? What can be shared and what can’t be. How do you work with external partners and protect your content?
We can document your data policy, prepare your data privacy policies, incident response plans and data management structures, and we can set up compliance regular reporting.
We’ll implement the policies in your 365 and manage your data to make sure it’s where it should be, not suffering from duplication confusion or unintended leakage
Data Management
The tidier your data, the easier it is for AI to use it well to accelerate your productivity
Download our latest executive “10 minute” briefing to share with colleagues

Latest Cybersecurity Insights & Resources
Zero-Trust IT Security
'Zero-Trust' is a tough headline. Zero-trust in a world where we trust people all the time is an unpleasant concept. We trust that when we order a package online, that the vendor will take our order and not just our money, that our product will be passed to a courier...
HAFNIUM Microsoft Email Attack
Over the last few days, you may have read about a zero-day attack impacting Microsoft Exchange Servers. We became aware of this vulnerability on Wednesday last week (it was discovered on the 2nd in the USA so we were on to it immediately, allowing for time-zones) . ...
5 simple steps to stay cloud-cyber-secure
We’ve posted repeatedly about cyber-security and the need to be more vigilant and more careful, and we’ve shared real-world stories to reinforce the concern. It’s a concern then that we still see a number of organisations that remain reluctant to increase their...
Cyber-risk mitigation – why Multi-Factor Authentication (MFA) is vital, but NOT enough
We keep making the point that nothing can guarantee you won’t be hacked. But you can, and must, mitigate your cyber-risk. We think tools like Multi-Factor Authentication is crucial for protecting your IT systems – and MFA should be on EVERYTHING you use – your email...
The Worst Hack in US History
In the last week, we’ve seen two major successful attacks on critical US IT management and Cyber security tools. The first we learned about was on FireEye which is one of the leading and most trusted cyber security tools, used by much of the Fortune 500. ...
Look out for more ransomware in 2021
2020 saw a crazy amount of ransomware attacks. We've warned repeatedly of the increasing sophistication and organisation of these bad actors. Names like RangarLocker and Dharma are cyber-businesses or do it yourself cyber-crime kitsets designed to cause havoc for...
DDOS – Distributed Denial of Service Attack (aka what went wrong at the NZ Stock Exchange)
Denial of Service (aka what went wrong at the NZX?) In September the NZ Stock Exchange was the victim of an attempted extortion via a DDOS attack. The attack took them offline serval times over a number of days. Many business are now asking, what is DDOS and could...
Keeping our Security tools up to speed
Cyber-crime is estimated to earn criminals US$7 Trillion a year That sort of money buys cyber criminals a lot of resources. It’s no surprise then that cybercrime has its own support industries. You don’t need to access the "Darknet" to purchase hacker tools. Many...
GOOD PROCESS WASN’T GOOD ENOUGH – SCAMMERS STILL WON
In August we all heard about Team NZ falling prey to a $2.8 million invoice payment fraud. It was the now-familiar story of a fake or hacked email, asking for payment to go to a different bank account. We should all be familiar with these tales by now. I’m sure that...
What is Double Key Encryption and why should you care?
Double Key Encryption (DKE) is coming soon to Microsoft 365 (E5 plans required) Like the name suggests, this is even MORE secure than the levels of encryption previously seen. Microsoft are saying that you need it if: You want to ensure that only you can ever decrypt...