It has taken a while, but hackers have now figured out that they can target users via Teams chat.

There are legitimate reasons to chat with external parties, but, as with all forms of digital communication, you need to be alert.
CyberThreat Summary
Researchers at ReliaQuest have uncovered a new social engineering technique employed by “Black Basta” ransomware actors to gain an initial foothold into victim environments.
Previously, these actors would overwhelm users with email spam, prompting recipients to create a legitimate help-desk ticket to resolve the issue. From here, Black Basta operators would then contact the end user, posing as the help desk to respond to the ticket.
In the latest intrusions observed by ReliaQuest, Black Basta actors have started to use Microsoft Teams chat messages to communicate with targeted users. In this case, targeted users are added to a Microsoft Teams chat with external users, who pose as support, admin, or help-desk staff. Their profiles are set to a display name designed to trick the targeted user into thinking they are communicating with a genuine help-desk account.
According to researchers, targeted users are sent QR codes within these chats, masquerading as legitimately branded company QR code images. While it’s unclear what the QR codes are specifically used for, researchers suspect that the end goal is to lead the end user to download remote monitoring and management tools like Anydesk and ultimately ransomware.
Analyst comments
The use of Microsoft Teams and QR codes represents a strategic approach employed by Black Basta actors to circumvent traditional email security measures. By exploiting Microsoft Teams, these actors aim to blend seamlessly with legitimate network traffic. Additionally, QR codes have emerged as a favored method for distributing malicious payloads. Most security tools that scan for text or hyperlinks are not capable of analysing the embedded data within QR codes, incentivising these actors to disseminate them via email and platforms like Microsoft Teams as a means to evade detection.
Mitigation
Recommendations from ReliaQuest:
- To mitigate against tactics involving Microsoft Teams and QR code phishing, organisations can disable communication from external users within Teams to prevent unwanted chat messages from reaching end users.
- Block suspect Teams callers, and warn your colleagues about the threat
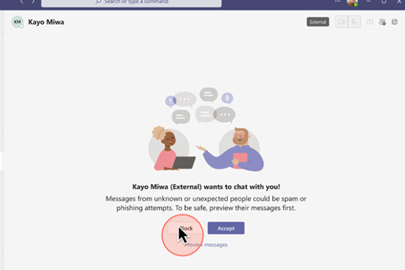
- When communication with external users is necessary, specific trusted domains can be allowlisted. Additionally, setting up aggressive anti-spam policies within email security tools can prevent spam from inundating end users’ inboxes. Limit the feature to as few people as possible and provide awareness training.
- Ensuring that logging is enabled for Teams, particularly the “ChatCreated” event, will facilitate detecting and investigating such activities.
- Microsoft Teams accounts impersonating IT help desks typically have their names set to “Help Desk.” This string is often surrounded by whitespace characters, likely to center the name within chats. When searching for these accounts, organisations should search for “contains,” rather than a direct match.
- The post-exploitation activities linked to these tactics are neither new nor unexpected. Existing detection rules and security tools are well-prepared to address these threats.
For more information, refer to https://www.reliaquest.com/blog/black-basta-social-engineering-technique-microsoft-teams/

