Password Vaults and You
With more and more websites necessary for our everyday activities, it’s getting harder and harder to manage passwords. By now, you will know not to write passwords on post-it notes and paste them on your screen. It’s not uncommon for most people to use the same username and password on a number of sites, particularly on sites we think are less important – for example, hotel websites or some news sites. However, this is a dangerous game to be playing with your information and cyber security.
The problem is that when (not if) your information gets breached, your username and password get into the hands of bad actors who poke and prod other sites on the internet, and test where else you may have used one of these passwords, or a simple variation.
Of course, this is a cyber security challenge. We cannot easily remember hundreds of passwords, especially complex ones. We need an easy way, and we have a solution. A password vault.
But then the question you will ask is, “what happens if the vault is breached?” You need a super-secure vault. Something that easily remembers, (and creates) complex passwords for you and your colleagues – personal and work – and operates on Windows, Mac, and mobiles. It needs to be SOC2 certified so you know it’s secure.
What can a password vault offer you?

- No more remembering dozens of passwords
- Faster access to websites and applications
- Centralised system for both corporate and personal passwords
- Folders to organise and categorise credentials
- Automatic generation of audits and reports to help with tracking and compliance
- Improve the cyber security you provide your colleagues by promoting a password management system you trust
- Use strong password strings to thwart hackers
- Receive a notification of all the passwords of departing employees so clients can remove their access to company systems
- Give clients the tools to granularly grant employee access to employee systems and networks
- Meet compliance measures with comprehensive auditing and reporting capabilities
- Users can access their Site credentials quickly and easily through the native mobile apps on iOS and Android®, auto-fill to log in to websites, and apps on mobile devices
- Cross-browser extension for Google, Chrome, FireFox, Edge, and Chromium-based browsers
What’s your next step?
We’ve created a simple 9-point checklist to help you navigate the cyber-risk landscape and find the right digital security solution for you.
Kinetics can offer you a KARE Password Vault as part of KARE for Security S2 plan or you can subscribe to this standalone for $20 + GST per month for 5 users
Find out more about our Cyber Security Plans here
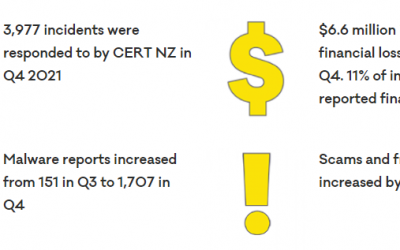
Hot off the press – we have just received CERT NZ’s report for the last quarter of 2021
So, just a quick reminder of who CERT NZ are – it’s the official NZ Government Cyber-Security agency. So, first up – 13% increase in reported incidents on the previous year and a big spike into the last quarter. 9% more phishing attacks. 24% more malware, based on the...
When hacking can help.
Ukraine is pretty well known for tech innovation. In fact it was worth $US6.8 Billion last year Ukraine’s Booming Tech Outsourcing Sector at Risk After Russian Invasion - WSJ. On top of that ‘legitimate’ work, Ukraine has also been home to some of the...
Sigh! How dumb and immoral can hackers get?
You can only sigh! We are witness astounding bravery and inspirational leadership in the Ukraine. We are watching the unfortunate abandoning everything they have built up to become refugees as they flea the dangers. The world is heartbroken. But amongst us there are...
Latest trend – hacking Teams
Over a quarter of a billion people use Teams every month. Under the current lockdown/isolate/work-from-home regimes, it is a vital tool for most of us. Many organisations including us even use it for our phones because it is so flexible and excellent value. You can...
2021 Trend Reports confirms cyber-security advice
How many people DON’T report ransomware attacks? It’s too early to see the Q42021 results from CertNZ but their Q3 report tells there were 2,072 incidents that they responded to in Q3 and fraud/scam’s were up 25%. Their report confirms that the very risks we have been...
Hackers Caught! Millions Seized
Crime doesn’t always pay. The FSB reports (if you can read Russian) that they have taken down the “Revil” band of hackers. These are the people that have caused absolute havoc, from disrupting the US oil pipelines, to the Kaseya attack that took out businesses all...
Do you need to worry about the “Log4J” Cyber Security Zero-Day breach?
Mainstream media is abuzz with the latest software vulnerability. It is in a commonly used component called Log4J 2. This component is in widespread use and the risk is real. This is a fast paced and quickly changing alert. At the time of writing, the immediate...
What’s worse than having to pay Ransomware?
The answer : Having to pay it twice - (or even more). Your Cyber-Security is under more pressure than ever. According to Infosecurity magazine, "double" extortion ransomware victims are up a massive 935% - thats a ten-fold increase year-on-year. This is driven by the...
“Phishmas” – its not that punny
Whatever it takes to draw your attention to Cyber Security is worth it. Just because we take time off at Christmas doesn't mean the hackers do. They have taken a lot of heart from the way we have all embraced home-delivery for our shopping and are doubling down with...
Is your Fingerprint effective security?
Straight out of the movies We are all used to the idea of using our fingerprints to log into our cell phones and, for some of us, our laptops. We’ve been told fingerprints are secure, and effective for ‘biometric authentication’ In the movies, we see finger prints...