This is a great example of needing new tools that didn’t used to exist, to keep cyber-safe, even if they add cost to our cyber-protection.
Hijacking your trust in LinkedIn
Cybersecurity firm Cofense have detected phishing campaigns that used LinkedIn links called “Smart Links” to bypass security gateways for deliver credential phishing.
Smart Links are used by LinkedIn Sales Navigator and other business users to track content and engagement. A smartlink is the mysterious 8 character code in a LinkedIn URL at the end.
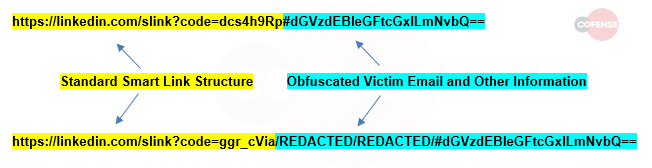
Fig 1 Cofense SmartLink structure
We’re told that the hacker code uses this to read from the attached email and use that to present a fake Microsoft login page.
If they can convince you to put in your details, and to enter your MFA code, then voila, they have access to your 365.
Because it’s using the LinkedIn URL, and we all tend to trust LinkedIn, your email filter is blindsided. It is not something we can easily filter out because LinkedIn is a trusted domain.
That means the victim recieves a legitmate looking email, with a link they are enticed to click on, that opens a fake Microsoft 365 which includes the victims email address so it looks even more authentic.
Kinetics KARE is stepping up
The Kinetics KARE team are testing a brand new tool that helps isolate login pages in a virtual sandbox to test them and filter out fakes. It is brand new technology. Subject to testing, this will be deployed to our Kinetics Security Plus premium service.
