The Trillion dollar industry
At the time of writing, the Waikato DHB cyber-attack is ongoing. The government is refusing to pay the ransom as a point of principle, and it looks like every possible tool at their disposal is being used to try to recover the situation.
Should they just pay the ransom? Or should the government go further and make it illegal to pay ransoms in New Zealand? That’s the question that Minister Kris Faafoi is having to assess at the moment. DHB attack: Why Justice Minister Kris Faafoi won’t make it illegal to pay a cyber-ransom – NZ Herald
Cyber crime is big business. We’ve called it organised crime in previous articles and we’re happy to stick with that. These organisations recruit the best and brightest out of the top universities, and give them both the latest tools and time to wreak havoc. Their recruits are paid astronomical sums to work for them, overcoming any moral objections with immorally large pay checks. These paychecks are funded by the proceeds of previous hacks. Every time they are paid, their war chest is strengthened. For example, we recently saw the Colonial Pipeline in the eastern US get hacked for 75 bitcoins (just under US$4M) which went to a criminal group called ‘Darkside”.



So, will cutting off payments stop their attacks by removing the incentive?
These criminals are smart and highly motivated. They seem to have no conscience but plenty of greed. Waikato is not only the hospital being brought down – there was a huge wave of hospital attacks in the US in October, just a few months ago – Several hospitals targeted in new wave of ransomware attacks – CNNPolitics.
I don’t know how Waikato DHB got infected, but the rumour is that it was from phishing attacks onto machines that weren’t fully patched up to date. We don’t know if that is true, but it is a common attack vector. Once a hacker gets into a system, they often hold back and try to dig further looking for more vulnerabilities they can exploit. The more damage they can cause, the more ransom they can demand, so they will often use one vulnerability to find the next, and so on until they finally have enough to bring the house down.
Security is all about layers. There is NO way to prevent attacks, and it is impossible to guarantee that any system is invulnerable. We saw that with the recent Hafnium attack where a vulnerability was exploited before patches were available to block it. But the more layers of security, the harder you make it, and you reduce the scope of any harm.
Today, even if you have the best backups and can recover the system, the hackers then threaten to release the data you hold to media or competitors. In the case of the Waikato DHB, it is being reported that personal data is being released to media by the hackers to increase pressure, even as they fail to stand their systems up.
As to paying the ransom, I suspect your perspective changes when your business, your job or livelihood is threatened. Not an easy decision and hopefully one we can avoid by being paranoid.
The best solution we can recommend is to check your cyber insurance and to apply the best security you can reasonably afford, which should be more than you had last year. Expect it to be more again next year as new tools and new threats emerge. Consider managed security solutions like our KARE Plans.
We don’t know where this will end, or if it will end, but let’s hope so. It is such a drain on our resources and holds us back from investing in tools that make us more productive.
Webinar Replay: Rethinking Endpoint Security: Smarter Strategies for a Safer Business
Cyber-protection keeps getting more complex, more restrictive and more expensive. This month we are talking with expert Thomas Shobbrook. He updates us on the latest security trends and help us understand how well protected your device is out-of-the-box. We ask...
Webinar Replay – Securing the Mobile Frontier: Cybersecurity Essentials for Phones and Tablets for Modern Businesses
As mobile devices become the backbone of modern business operations, they also present a growing target for cyber threats. Apple or Android - they're both important. Every time you use these to access your Teams, Email or anything else, you are relying on them to be...
Device Code Phishing: A Dangerous New Scam You Need to Know About
Device code phishing is a sneaky new way hackers are stealing people's online accounts. In device code phishing, threat actors exploit the device code authentication flow to capture authentication tokens, which they then use to access target accounts, and further gain...
June 2025 Report: Cyber is now the THIRD largest economy in the world
As we approach the midpoint of 2025, New Zealand’s cyber security landscape continues to evolve rapidly. With digital transformation accelerating across sectors, the country faces a growing array of cyber threats—ranging from financially motivated scams to...
Webinar Replay -Enhancing Your Security Posture with Microsoft Secure Score
This webinar replay covers the essentials of Microsoft Secure Score. Secure Score is a powerful tool designed to help businesses assess and improve their security across Microsoft 365 workloads. We will explore what Microsoft Secure Score is, why it is crucial for...
Webinar Replay – 5 mistakes people often make with passwords and how to overcome them
Passwords are the first line of defence against cyber threats. However, many people still make common mistakes that leave their accounts vulnerable. Watch this video for a 30-minute webinar where we will discuss the most frequent password pitfalls and how to avoid...
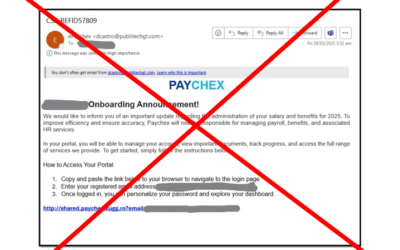
Who’s been paying attention?
We’re really proud of our clients! Last week, these little pieces of ill-intentioned mischief popped up for a couple of the businesses we look after.They were smart enough to evade anti-spam software but not the cyber-training. Although the emails look legitimate,...
Don’t let these common security gaps take your business down.
We’re only a few months into 2025, and already we’ve seen businesses hit hard by cyberattacks they could have prevented. Every time we conduct IT security checkups, we find the same critical vulnerabilities—gaps that could lead to serious downtime, data loss, or...
NCSC warns law firms
It’s not surprising that legal practices are targeted by cyber-criminals.By their very nature, they hold considerable amounts of private “PII” data (personally identifiable information). On top of that, law firms are typically busy, pressured environments where it is...
Webinar Replay – What are the NZ Government recommendations for SME Business cyber-security?
What are the NZ Government recommendations for SME Business cyber-security? How does your business match up?CertNZ has been rolled into the new National Cyber Security Centre. They've released the 10 Critical Controls and a Cyber-Security Framework? What do they mean...