If you don’t where it is, you can’t protect it.
Do you know where ALL your organisation’s data is – not physically, but on which web and cloud services?
Here’s the problem. If you don’t where it is, then you can’t protect it. The secondary problem is finding out, because not everyone in your organisation will be onboard. It is common for people to sign up to web services because they offer something useful that helps them do their job.
They sign up using their email address and creating a password. There is the first headache – how does anyone track what has been signed up to across your organisation, let alone who has access to it? If that person leaves, no one will change the account credentials if they don’t know about it, but your ex-colleague still has access.
Secondly, what data do they upload? Is that data that you have a legal or moral responsibility for?
There’s nothing noble about Nobelium.
This isn’t theory – it’s real. USAID is a pretty important US organisation – promoting democracy and human rights around the world. Turns out, someone there was using a well-known email database tool called Constant Contact. But their account wasn’t well protected. Worse still, their account had a huge mailing set up, and of course, it had all the official USAID templates.
So, these Nobelium people, allegedly a Russian state-sponsored hacker group, compromised the Constant Contact account and sent a bulletin out. The bulletin contained malware that allowed the hackers to take command and control over victims computers. Ironically the fake email alleged interference in the US federal elections.

So, what can you do?
The first step is knowing what SaaS tools your people are using. We call this SHADOW IT and it is inevitable. Rather than stopping it, the job IT has is to identify it and manage it. The second step is to secure those platforms. That’s why our KARE for Security S2 plan contains a useful tool to help you identify what services your people are using.
Refer : What We Know About The Apparent Russian Hack Exploiting USAID : NPR
Webinar Replay: Rethinking Endpoint Security: Smarter Strategies for a Safer Business
Cyber-protection keeps getting more complex, more restrictive and more expensive. This month we are talking with expert Thomas Shobbrook. He updates us on the latest security trends and help us understand how well protected your device is out-of-the-box. We ask...
Webinar Replay – Securing the Mobile Frontier: Cybersecurity Essentials for Phones and Tablets for Modern Businesses
As mobile devices become the backbone of modern business operations, they also present a growing target for cyber threats. Apple or Android - they're both important. Every time you use these to access your Teams, Email or anything else, you are relying on them to be...
Device Code Phishing: A Dangerous New Scam You Need to Know About
Device code phishing is a sneaky new way hackers are stealing people's online accounts. In device code phishing, threat actors exploit the device code authentication flow to capture authentication tokens, which they then use to access target accounts, and further gain...
June 2025 Report: Cyber is now the THIRD largest economy in the world
As we approach the midpoint of 2025, New Zealand’s cyber security landscape continues to evolve rapidly. With digital transformation accelerating across sectors, the country faces a growing array of cyber threats—ranging from financially motivated scams to...
Webinar Replay -Enhancing Your Security Posture with Microsoft Secure Score
This webinar replay covers the essentials of Microsoft Secure Score. Secure Score is a powerful tool designed to help businesses assess and improve their security across Microsoft 365 workloads. We will explore what Microsoft Secure Score is, why it is crucial for...
Webinar Replay – 5 mistakes people often make with passwords and how to overcome them
Passwords are the first line of defence against cyber threats. However, many people still make common mistakes that leave their accounts vulnerable. Watch this video for a 30-minute webinar where we will discuss the most frequent password pitfalls and how to avoid...
Who’s been paying attention?
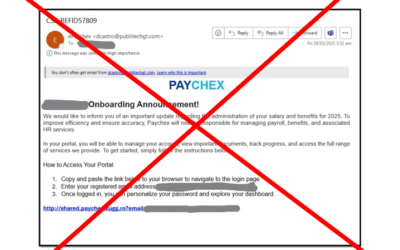
We’re really proud of our clients! Last week, these little pieces of ill-intentioned mischief popped up for a couple of the businesses we look after.They were smart enough to evade anti-spam software but not the cyber-training. Although the emails look legitimate,...
Don’t let these common security gaps take your business down.
We’re only a few months into 2025, and already we’ve seen businesses hit hard by cyberattacks they could have prevented. Every time we conduct IT security checkups, we find the same critical vulnerabilities—gaps that could lead to serious downtime, data loss, or...
NCSC warns law firms
It’s not surprising that legal practices are targeted by cyber-criminals.By their very nature, they hold considerable amounts of private “PII” data (personally identifiable information). On top of that, law firms are typically busy, pressured environments where it is...
Webinar Replay – What are the NZ Government recommendations for SME Business cyber-security?
What are the NZ Government recommendations for SME Business cyber-security? How does your business match up?CertNZ has been rolled into the new National Cyber Security Centre. They've released the 10 Critical Controls and a Cyber-Security Framework? What do they mean...