KARE Security Plus
Take security seriously.
Managed Detection and Response service with a 24 x 7 Security Operations Center (SOC).
KARE Security Plus is a step up and includes everything in the KARE Security Foundation Service. It is critical for organisations who take cyber security seriously. Get in touch, and we can show you examples where KARE Security Plus would have saved companies hundreds of thousands of dollars from hacks, if only they had this level of security.
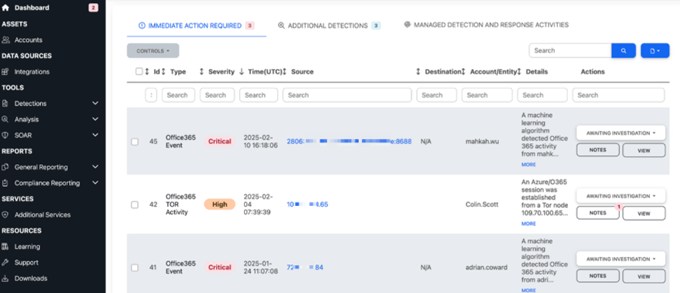
Real-time Detection Alerts
Automated analysis and response., speeds up detection and shortens the time to react.
Comprehensive Response Capabilities
Security experts respond 24x7x365 to take protective action within your environment.
Achieve Compliance Requirements
Automated compliance reporting is available for PCI DSS, NIST and HIPAA.
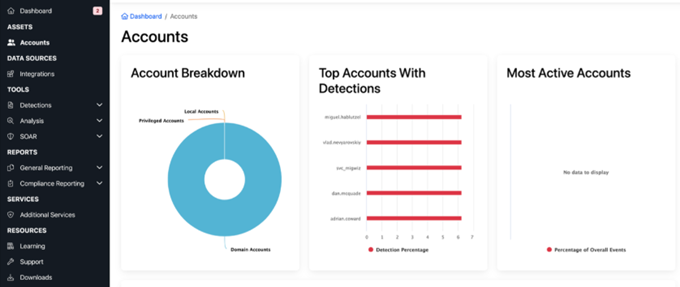
Privilege Analysis of Network Accounts, Systems and Groups
Privilege analysis of every account, system, user can know who access what and when.
Analysis and Recommendations
Expert analysis and recommendations for confirmed incidents including timely and appropriate counter measures.
Security events are collated from agents running on your Windows and Mac devices, Honey Pot Networks (If you have Hyper-V or VMware infrastructure), Microsoft Active Directory Domain Controls, KARE EDR and your Microsoft Azure/365 Environment. Automated fast reaction responses keep you ahead of the hackers. Experienced analysts undertake threat hunting and will take protective action to secure your devices and data.
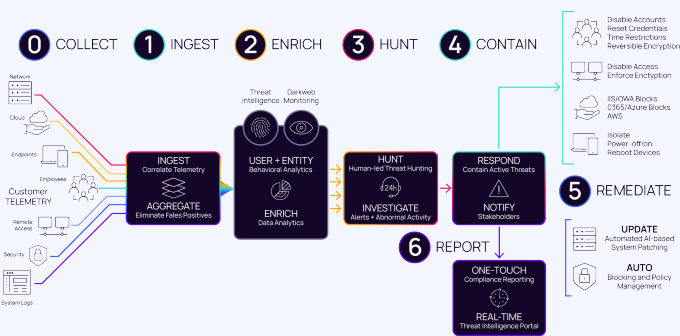
Security events are held in the for 30 days. An option is available for 90 day retention.
KARE Security Plus.
Always on duty
Security Events Gathered and Analysed.
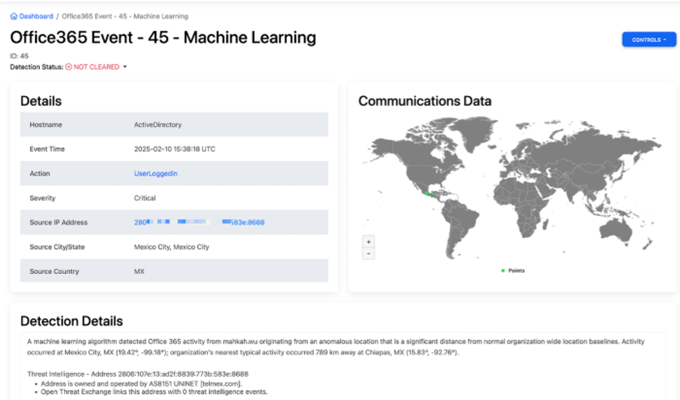
At the center of KARE Security Pus is an SIEM (Security Information and Event Manager). This is where security events come together. Analysis is undertaken of events from all sources and devices giving a rich contextual view of what is happening on your network. Analysis makes use of Machine Learning and AI to identify suspicious patterns and behaviors.
Powerful automated systems are supported by security experts. They can undertake further analysis and threat hunting. Included in KARE Security Plus is protective action. Automation and/or experts can isolate machines and lock down/out accounts.
Windows and MacOS Agents
The lightweight agent runs on your Windows and Mac devices (A Linux agent is also available). It gathers security events which are then sent to the SIEM for analysis. The agent is also Windows Domain aware and gathers security information from your Windows Active Directory.
Honey Pots
A Honey Pot is a virtual network device that runs in your environment. To hackers it looks like a tempting target. The KARE Security Plus Honey Pot can run in a Hyper-V or VMware Environment. Attempts to scan the Honey Pot will trigger events with in the SIEM.
KARE EDR
KARE EDR (Endpoint Detection and Response) is a state-of-the-art protective software solution that is included in KARE Security Foundation. KARE Security Plus adds to this by importing security events into the SIEM. It combines with Endpoint, Honey Pot, Active Directory and Microsoft 365 events to identify lateral movement and abnormal events.
Microsoft AZURE/365
Microsoft 365 is an essential business tool powering business around the globe. Its widespread business use attracts the attention of bad actors. These vital business environments are under attack 24 x 7 x 365. KARE Security Plus delivers essential, automated protection against account compromises in M365 environments. By leveraging behavioral analytics and correlating M365 event data, KARE Security Plus detects early indicators of suspicious activity and potential breaches. The system then responds automatically with Security Orchestration, Automation and Response (SOAR) actions, such as triggering password resets or disabling accounts. This ensures that threats are swiftly neutralised before they can cause harm. A team of professional analysts will take charge of responding to detected threats and conducting in-depth investigations to identify their root causes. This proactive approach helps implement effective mitigation strategies and reduces your overall attack surface.
The following is a list of sample Breach Preventions within Microsoft 365 alerts.
A. Sign-in and Authentication Alerts
- Unusual Sign-in Activity – Detects logins from atypical locations or devices.
- Multiple Failed Sign-in Attempts – Indicates potential brute-force attacks.
- Impossible Travel Activity – User logs in from two distant locations within a short time.
- Sign-ins from Known Malicious IPs – Identifies login attempts from blacklisted IPs.
B. Suspicious User Behavior Alerts
- Privileged User Account Anomalies – Unusual activity from admin accounts.
- Excessive Access Requests – Multiple access requests to sensitive systems.
- User Added to High-Privilege Group – Detects unauthorised privilege escalation.
C. Threat Intelligence-Based Alerts
- Communication with Malicious IPs/Domains – Traffic to known threat actors.
- Malware Beaconing Detected – Signs of a compromised system communicating with a C2 server.
- Phishing Email Clicked by User – Identifies users who clicked on phishing links.
D. Endpoint and Malware Alerts
- Ransomware-Like Behavior Detected – Identifies mass encryption of files.
- Suspicious PowerShell Execution – Detects script-based attacks.
- Unusual Process Execution – Flags processes matching malware patterns.
E. Network and Cloud Security Alerts
- Unusual Data Transfer to External Locations – Possible data exfiltration.
- Multiple VPN Logins from Different Locations – Potential account compromise.
- Suspicious Azure Resource Deployment – Detects rogue VM or service creation.
F. Office 365 & Email Threats
- Mass Email Forwarding Rule Created – Possible insider threat or BEC attack.
- Suspicious File Sharing via OneDrive or SharePoint – Data leakage risk.
- Unusual Email Sending Patterns – Signs of compromised mail accounts.
How it works:
Real-Time Monitoring and Correlation of M365 Events:
KARE Security Plus seamlessly integrates and continuously monitors user and application activity within your M365 environment. This includes sign-ins, account modifications, enterprise application changes, and more. By correlating this data, KARE Security Plus can identify deviations from expected behaviors and assess the risk of a potential compromise.
Behavioral Analytics for Risk Detection:
Through UEBA (advanced behavioral analytics), KARE Security Plus detects abnormal user activities, such as sign-ins from unexpected locations, multiple failed login attempts, or the creation of unusual enterprise applications. These behaviors can often signal an account takeover or other malicious activity.
Automated Response to Minimise Impact:
When KARE Security Plus detects high-risk activity, it automatically takes action. If it identifies a potential compromise—such as a suspicious login attempt from a malicious or anonymous IP address—it can automatically reset the account’s password or disable the account to block further unauthorised access. The system uses contextual information to make precise decisions about the severity of the event and the appropriate response.
Comprehensive Event Detection:
KARE Security Plus analyses a wide range of events and behaviors within M365 to detect potential breaches. Some key detection categories include:
Suspicious Sign-In Activity:
Unusual sign-in attempts, especially from unknown or malicious IP addresses, failed login attempts, or behaviors associated with password spraying.
Changes to Security Settings:
Unexpected changes in critical settings, such as modifications to MFA policies, permissions on service principals, or adjustments to security configurations that could signal malicious intent.
Application-Level Threats:
Detection of unauthorised access to user mailboxes or changes to enterprise applications, which can be indicators of malicious persistence mechanisms.
Email-Related Risks:
Indicators such as email forwarding or redirection rules, often set by attackers to exfiltrate sensitive information, or suspicious inbox rules that obscure an attacker’s activities.
Excessive Account Privileges:
Provides visibility into misconfigured accounts with excessive privileges that could allow for unauthorised access.
Why its Valuable:
Comprehensive Threat Detection:
KARE Security Plus offers thorough monitoring by correlating multiple M365 event data points to identify potential breaches early. From suspicious sign-in attempts to changes in security settings, ensuring you’re aware of threats that may otherwise go undetected.
Fast, Automated Incident Response:
With automated response capabilities, KARE Security Plus automatically takes immediate action to mitigate risk when it detects suspicious activity. This ensures that any compromised accounts are quickly neutralised without requiring manual intervention.
Always On Protection:
Your M365 environment is available 24x7x365. KARE Security Plus includes security professionals undertaking threat hunting around the clock. They focus on core security needs, protecting user accounts, maintaining a robust security posture.
Enhanced Compliance & Visibility:
KARE Security Plus automatically logs all detected activities and responses, creating a comprehensive 30 day audit trail. This helps with compliance and reporting, making it easier to meet regulatory requirements and investigate security incidents when needed.