One of our clients recently found themselves dealing with one of the most brazen hack attempts I’ve heard to date.
They’d heard from one of their customers that they (the customer) had taken a phone call purporting to be from our client, to say they’d changed bank accounts. They asked the end customer to please pay invoices to the new bank account that they gave over the phone! The number the call came from appeared to be a local one.
Luckily, the end-customer was suspicious and called back! We found that the call had been routed through a local VOIP number so it appeared to be local, but was clearly from overseas. We don’t know how the hacker found the relationship between the end-customer and our client, but that could be pretty easy – for example an online testimonial would do it. (We did find the end-customer had been pwned, but that’s true of most of us).
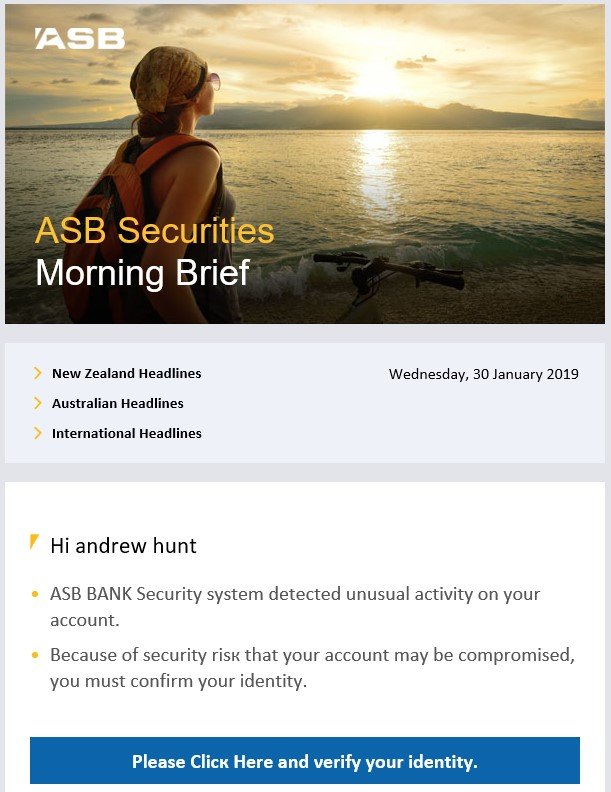
So that’s a first! But the regular phishing attacks carry on and just yesterday, I got an apparent warning in my inbox from the ASB. As you can see, it looks authentic! If you click on the link, the screen that opens looks like the real thing.
That was a bit embarrassing for me as I was showing someone how the link would be blocked, but instead our first level of defense failed – the standard Microsoft safelinks security which is normally pretty good.
However, proving the value of multiple layers of defence, our premium “[wow_colorme]KARE for Security[/wow_colorme]” system did detect and prevent it.
One of the challenges that these tools face is just how quickly these sites appear and are sent out, and of course they also have different goals behind them – generally either to infect your system with cryptoware, or to get you to hand over private information.
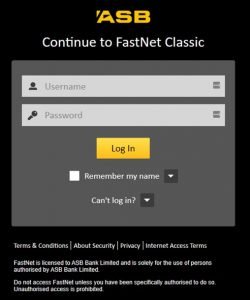
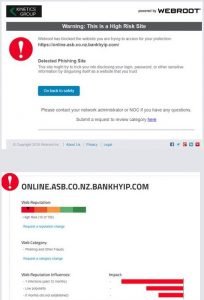 By the way, we’ve sent a copy to the ASB’s excellent cyber security team to warn them, although I doubt there is much they or anyone can do about it.
By the way, we’ve sent a copy to the ASB’s excellent cyber security team to warn them, although I doubt there is much they or anyone can do about it.
So, this raises the question – what can you do?
Tempting as it is to revert to pen and paper, that’s not a realistic option!
Instead, we would suggest tools like KARE for Security that add layers of protection, so if one layer is breached as in this example, there are others with slightly different algorithms that may catch it. We think training and phishing tests are vital to raise awareness and caution. But finally, we would also note that being caught by these is almost inevitable for any busy person. So great backups are vital, insurance is recommended and an open approach that encourages people to come forward.
