Over the last month, we’d heard about this happening in the US and now it seems to be happening in NZ as well. Cyber insurers are working hard to mitigate their risk and that includes stepping up their testing of their clients.
Right now, that appears to be more focussed on their client’s websites, but you can anticipate it will start to extend to more of your online assets, and especially trying to test against your remote access.
Of course, websites are an interesting challenge because in the main, they are managed by the web provider and not your main IT support partner (like Kinetics). There are some exceptions, but the majority of websites are about a brand presence, and they are reviewed periodically and maintained by the web developer or eCommerce provider.
We’re stepping up our attention to these, especially for KARE for Security subscribers. Those subscribers know we’ve been working hard to keep their systems secure and adding layers of protection. We are now looking to see what else needs consideration.
Back to the insurance. One of our clients got a surprise this week when their insurer sent them an unexpected report. It came as a bolt from the blue to the client, who had no awareness their insurer was scanning their website. Even more of a surprise was finding out how low their score was.
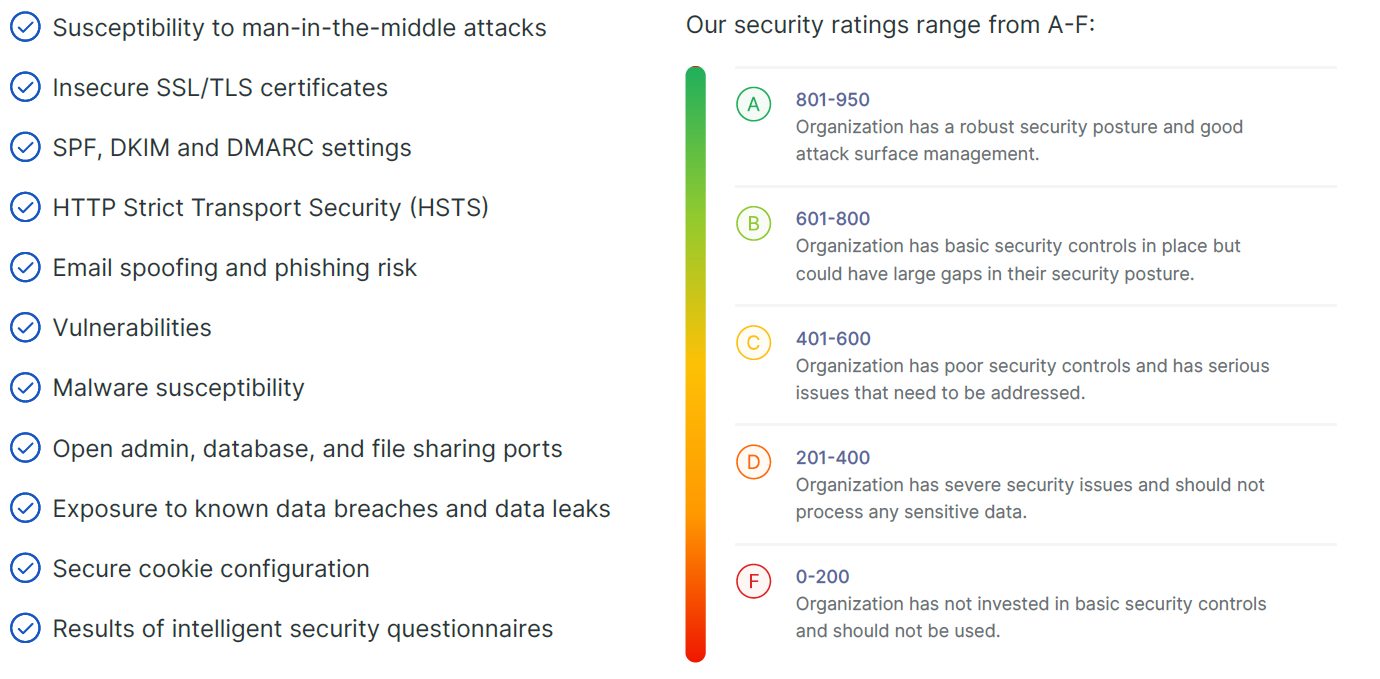
The insurer used a tool called UpGuard to scan the web presence across the following points.
In this case, their score was only 418 out of a possible 950. The insurer told their client that this was serious.
However, nothing is that simple. Firstly, its only a website made up of marketing material. All the client’s confidential information is held on their network, and we’re confident that is as secure as is reasonable.
Secondly, the insurer scanned an IP address that holds websites for many of the web-hoster’s clients, with a variety of different services behind them. Who knows what else is running there for these clients?
However, there are things we can turn up the dial on. DNSSec, which we are testing at the moment, or DMARC, which can cause more problems when emails aren’t delivered. One thing that jumped out at us was the Open Ports which gives us the clue that its more about the web-hoster than the client and our take away from that was to prepare some protocols for our clients to share with their hosters to ensure they are as safe as is practical.
This story is a reminder that cyber-security is a journey rather than a destination.
It reminds us that what used to be enough isn’t adequate any longer, and new layers are needed all the time. Frustratingly, every new layer adds cost and inconvenience, but the most costly and inconvenient situation would be to suffer an attack.
