Password Vaults and You
With more and more websites necessary for our everyday activities, it’s getting harder and harder to manage passwords. By now, you will know not to write passwords on post-it notes and paste them on your screen. It’s not uncommon for most people to use the same username and password on a number of sites, particularly on sites we think are less important – for example, hotel websites or some news sites. However, this is a dangerous game to be playing with your information and cyber security.
The problem is that when (not if) your information gets breached, your username and password get into the hands of bad actors who poke and prod other sites on the internet, and test where else you may have used one of these passwords, or a simple variation.
Of course, this is a cyber security challenge. We cannot easily remember hundreds of passwords, especially complex ones. We need an easy way, and we have a solution. A password vault.
But then the question you will ask is, “what happens if the vault is breached?” You need a super-secure vault. Something that easily remembers, (and creates) complex passwords for you and your colleagues – personal and work – and operates on Windows, Mac, and mobiles. It needs to be SOC2 certified so you know it’s secure.
What can a password vault offer you?

- No more remembering dozens of passwords
- Faster access to websites and applications
- Centralised system for both corporate and personal passwords
- Folders to organise and categorise credentials
- Automatic generation of audits and reports to help with tracking and compliance
- Improve the cyber security you provide your colleagues by promoting a password management system you trust
- Use strong password strings to thwart hackers
- Receive a notification of all the passwords of departing employees so clients can remove their access to company systems
- Give clients the tools to granularly grant employee access to employee systems and networks
- Meet compliance measures with comprehensive auditing and reporting capabilities
- Users can access their Site credentials quickly and easily through the native mobile apps on iOS and Android®, auto-fill to log in to websites, and apps on mobile devices
- Cross-browser extension for Google, Chrome, FireFox, Edge, and Chromium-based browsers
What’s your next step?
We’ve created a simple 9-point checklist to help you navigate the cyber-risk landscape and find the right digital security solution for you.
Kinetics can offer you a KARE Password Vault as part of KARE for Security S2 plan or you can subscribe to this standalone for $20 + GST per month for 5 users
Find out more about our Cyber Security Plans here
What can you expect if you get crypto-locked?
!Right now, there’s a crypto-locked server in the lab in our Kinetics Auckland Office. It’s not from one of our clients, but a business that’s come to us, after the event, asking for help. We are busy rebuilding it and restoring the data and configuration to the...
Are you meeting the requirements of your Cyber Insurer? (And are you minimising your risk anyway?)
Given the scale of cyber-attacks, we aren’t surprised to be hearing reports of insurers applying a "duty of care" test before agreeing to pay out. Despite sending chills up your spine, when you consider this, it makes sense as Insurers do the same thing to vehicles,...
3 billion devices are at risk. Does that include you? (it probably does)
An actively exploited high severity "zero day" cyber-security exploit has been found in the Google Chrome web browser. With over 3 billion users it will take some time for the update roll out to everyone. Meanwhile, everyone who uses Chrome on their PC is...
MFA is important, but it is no silver-bullet.
There are no silver bullets. No one can guarantee you won’t be hacked, but we can make it harder. We can reduce your cyber-risk by taking reasonable steps to make it harder to hack you. The key is to have layers of security, and to keep reviewing the technology in use...
Disaster at Kinetics
Sometimes, it feels like there is only bad news. All businesses face challenges with suppliers, our own people and even some of our customers. As managers, we work hard to get ahead of issues and create systems to mitigate problems, but there’s always something. ...
MS OFFICE ZERO DAY ATTACK – MAY 31st
One of the scariest news items to wake up to is that there is a ‘zero-day’ vulnerability in a common piece of software. That means that the hacking community has found an opportunity to hack a bit of software and there is no update yet – ‘zero’ days to apply a fix....
Beware – When Anti-Money Laundering (AML) CREATES a risk
That’s right. AML is not only frustrating to many of us, but it has also created cyber-risks. The irony isn’t lost on us. We’re honoured to support a large number of NZ law firms as clients, and it is a responsibility we take very seriously. Law firms handle such a...
Is MFA driving you mad?
Getting tired of having to open your phone for access? If so, you are not alone! But, its necessary. Hackers are counting on you suffering from an excess of having to reach for your phone to approve access, with something called “MFA Fatigue Attacks”.MFA Fatigue...
When QR codes go bad
Thanks to Covid, we’re all familiar with QR codes. Of course, with Covid, we were using the official tracer app to scan them, but in normal use, you can just use your phone’s camera to open the link. It’s a great way to make it easy to visit a website without having...
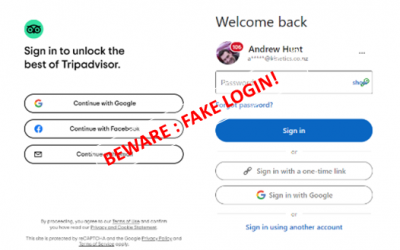
Is nothing safe? Fake logins!
Every day, there is a new cyber-threat to watch out for, and to warn friends and colleagues about. I’m frequently stunned when talking to friends and colleagues that these threats are abstract and academic. For the sake of absolute clarity, these cyber risks...