Data Leak Protection (DLP)
is the name of several policies in Office 365, setting up what data can, and can’t be, shared and with whom.
Imagine being able to automatically identify private information like passport numbers, Health IDs or bank account details and make sure that those are only being shared with people that are authorised to see them.
The good news is that you can do this with 365, provided you turn on the policies and set them up correctly, and monitor when data is shared.
Under the NZ Privacy Act, we’re all expected to take care of personal data entrusted to us and to make sure it’s only used for the purpose for which is being obtained.
With Office 365, there’s no excuse for that to be breached provided that we understand what data should be kept, what might be kept incorrectly, and how its being shared. With this we can set up rules to monitor your Office 365 system and report on how records are shared.
We include a basic set up of DLP in our KARE for Security S2 plan to get you started.

That day when a Kinetics client DIDN’T get hacked.
We’ve just wrapped up a security investigation for one of our amazing clients. All of our clients are amazing, but as you read this story, you’ll see why we’re especially proud of this client. We’ve anonymised it out of respect, although this story reflects really...
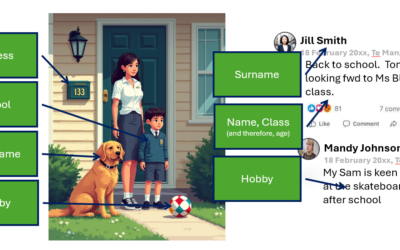
The Hidden Dangers of Oversharing Family Photos on Social Media
In today's online age, sharing family photos on social media has become a common way to stay connected with loved ones and document precious moments. But beware of ‘Oversharing’ There is a huge danger that this seemingly harmless activity can expose you and your...
TEN things the government says you need to know about your cyber-security defence
Regular readers will be a little tired of hearing us talk about cyber-risk and the threat of hackers. You'll forgive us a little because we see the impact when events happen, and we spend our days protecting our clients to keep them safe. But we're just a tiny cog...
What do Microsoft’s Upcoming 2025 Security Enhancements for Windows mean for you?
In response to the significant CrowdStrike meltdown last summer, which exposed some critical vulnerabilities in the Windows platform, Microsoft is set to introduce a series of further security updates in 2025. The meltdown, caused by a flawed update, led to widespread...
The Implications of Using ChatGPT (free gen-AI tools): An instructive Case Study from Australia
Recent news from Australia In a recent investigation, the privacy regulator in the state of Victoria has imposed a ban on the use of ChatGPT within a government department. This case highlights the dual nature of Generative AI (GenAI) tools, which offer significant...
Oh no, the worst has happened! Now what?
When we talk to people about the different risks that their organisation might face, one of the events that has the highest likelihood, and would have the biggest impact, is a significant cyber-event. The worst-case scenario would be a ransomware event, where the bad...
What is Malvertising?
Malvertising is appearing more frequently on search engines. More people are starting to experience frustration with search engines, partly due to occasional inaccuracies in AI-driven overlays and an excess of advertisements. Another emerging concern is “malvertising”...
Check out the NZ 2024 SME Cyber Behaviour Tracker
As cyber threats proliferate, small businesses find themselves not just in the crosshairs but also facing the daunting financial repercussions of a breach. There is an urgent need for robust cyber security measures. With the staggering average cost of $173,000 per...
Webinar Replay – Lessons from the recent “Largest Global IT outage in history”
Free Webinar Replay - What lessons can we learn from the recent outage?What lessons can we learn from the recent outage? How can we prevent these situations from happening to us? Join Kinetics CTO Bill Lunam and ConnectWsie's Leon Friend as they unpack what happened,...
Urgent Security Advisory (from Microsoft)
We have been alerted to an issue with some Microsoft Office products. The vulnerability is reported to be actively exploited and we expect Microsoft will expedite the release of fixes. Zero-day means that this is an immediate high risk and we are advised that it is...