If you don’t where it is, you can’t protect it.
Do you know where ALL your organisation’s data is – not physically, but on which web and cloud services?
Here’s the problem. If you don’t where it is, then you can’t protect it. The secondary problem is finding out, because not everyone in your organisation will be onboard. It is common for people to sign up to web services because they offer something useful that helps them do their job.
They sign up using their email address and creating a password. There is the first headache – how does anyone track what has been signed up to across your organisation, let alone who has access to it? If that person leaves, no one will change the account credentials if they don’t know about it, but your ex-colleague still has access.
Secondly, what data do they upload? Is that data that you have a legal or moral responsibility for?
There’s nothing noble about Nobelium.
This isn’t theory – it’s real. USAID is a pretty important US organisation – promoting democracy and human rights around the world. Turns out, someone there was using a well-known email database tool called Constant Contact. But their account wasn’t well protected. Worse still, their account had a huge mailing set up, and of course, it had all the official USAID templates.
So, these Nobelium people, allegedly a Russian state-sponsored hacker group, compromised the Constant Contact account and sent a bulletin out. The bulletin contained malware that allowed the hackers to take command and control over victims computers. Ironically the fake email alleged interference in the US federal elections.

So, what can you do?
The first step is knowing what SaaS tools your people are using. We call this SHADOW IT and it is inevitable. Rather than stopping it, the job IT has is to identify it and manage it. The second step is to secure those platforms. That’s why our KARE for Security S2 plan contains a useful tool to help you identify what services your people are using.
Refer : What We Know About The Apparent Russian Hack Exploiting USAID : NPR
3 billion devices are at risk. Does that include you? (it probably does)
An actively exploited high severity "zero day" cyber-security exploit has been found in the Google Chrome web browser. With over 3 billion users it will take some time for the update roll out to everyone. Meanwhile, everyone who uses Chrome on their PC is...
MFA is important, but it is no silver-bullet.
There are no silver bullets. No one can guarantee you won’t be hacked, but we can make it harder. We can reduce your cyber-risk by taking reasonable steps to make it harder to hack you. The key is to have layers of security, and to keep reviewing the technology in use...
Disaster at Kinetics
Sometimes, it feels like there is only bad news. All businesses face challenges with suppliers, our own people and even some of our customers. As managers, we work hard to get ahead of issues and create systems to mitigate problems, but there’s always something. ...
MS OFFICE ZERO DAY ATTACK – MAY 31st
One of the scariest news items to wake up to is that there is a ‘zero-day’ vulnerability in a common piece of software. That means that the hacking community has found an opportunity to hack a bit of software and there is no update yet – ‘zero’ days to apply a fix....
Beware – When Anti-Money Laundering (AML) CREATES a risk
That’s right. AML is not only frustrating to many of us, but it has also created cyber-risks. The irony isn’t lost on us. We’re honoured to support a large number of NZ law firms as clients, and it is a responsibility we take very seriously. Law firms handle such a...
Is MFA driving you mad?
Getting tired of having to open your phone for access? If so, you are not alone! But, its necessary. Hackers are counting on you suffering from an excess of having to reach for your phone to approve access, with something called “MFA Fatigue Attacks”.MFA Fatigue...
When QR codes go bad
Thanks to Covid, we’re all familiar with QR codes. Of course, with Covid, we were using the official tracer app to scan them, but in normal use, you can just use your phone’s camera to open the link. It’s a great way to make it easy to visit a website without having...
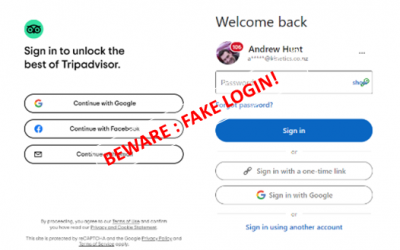
Is nothing safe? Fake logins!
Every day, there is a new cyber-threat to watch out for, and to warn friends and colleagues about. I’m frequently stunned when talking to friends and colleagues that these threats are abstract and academic. For the sake of absolute clarity, these cyber risks...
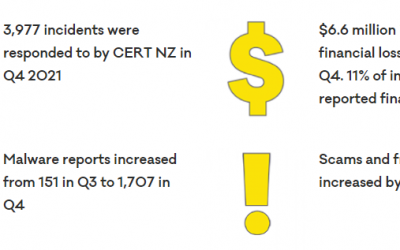
Hot off the press – we have just received CERT NZ’s report for the last quarter of 2021
So, just a quick reminder of who CERT NZ are – it’s the official NZ Government Cyber-Security agency. So, first up – 13% increase in reported incidents on the previous year and a big spike into the last quarter. 9% more phishing attacks. 24% more malware, based on the...
When hacking can help.
Ukraine is pretty well known for tech innovation. In fact it was worth $US6.8 Billion last year Ukraine’s Booming Tech Outsourcing Sector at Risk After Russian Invasion - WSJ. On top of that ‘legitimate’ work, Ukraine has also been home to some of the...