If you don’t where it is, you can’t protect it.
Do you know where ALL your organisation’s data is – not physically, but on which web and cloud services?
Here’s the problem. If you don’t where it is, then you can’t protect it. The secondary problem is finding out, because not everyone in your organisation will be onboard. It is common for people to sign up to web services because they offer something useful that helps them do their job.
They sign up using their email address and creating a password. There is the first headache – how does anyone track what has been signed up to across your organisation, let alone who has access to it? If that person leaves, no one will change the account credentials if they don’t know about it, but your ex-colleague still has access.
Secondly, what data do they upload? Is that data that you have a legal or moral responsibility for?
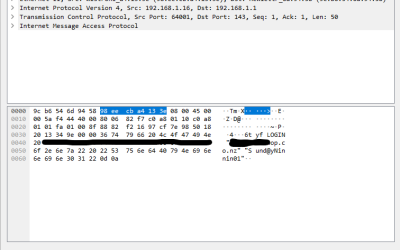
There’s nothing noble about Nobelium.
This isn’t theory – it’s real. USAID is a pretty important US organisation – promoting democracy and human rights around the world. Turns out, someone there was using a well-known email database tool called Constant Contact. But their account wasn’t well protected. Worse still, their account had a huge mailing set up, and of course, it had all the official USAID templates.
So, these Nobelium people, allegedly a Russian state-sponsored hacker group, compromised the Constant Contact account and sent a bulletin out. The bulletin contained malware that allowed the hackers to take command and control over victims computers. Ironically the fake email alleged interference in the US federal elections.

So, what can you do?
The first step is knowing what SaaS tools your people are using. We call this SHADOW IT and it is inevitable. Rather than stopping it, the job IT has is to identify it and manage it. The second step is to secure those platforms. That’s why our KARE for Security S2 plan contains a useful tool to help you identify what services your people are using.
Refer : What We Know About The Apparent Russian Hack Exploiting USAID : NPR
How secure is your cloud IT? Is it as safe as you expect?
Your cloud computing can be safe and secure, or open and vulnerable - the choice is yours. With the rise of hacker activity and cybercrime, it’s essential to lock down your cloud and protect it from threats. For most businesses, the standard 365 settings aren't...
What would you do Canterbury? Incident Response Workshop
Mastering Cybersecurity What would you do? Table-top exercise Join us for an interactive table-top simulation exercise. Imagine - you are busy going about your day when suddenly your meeting is interrupted. "No one can access their files" or "We just accidently paid...
Are your legacy IT systems giving hackers a backdoor into your business?
One of our engineers was working on migrating a customer from a legacy email server into Office 365 after we discovered they were under a brute force external attack. The migration required that we receive the users passwords. These would, of course, be reset after...
Service Alert
We're experiencing an extra heavy call volume today and it's proving challenging to respond as quickly as normal. It's been brought on by an apparent Microsoft change resulting in unexpected Windows 11 upgrades. These are happening to a number of devices even if...
Breaking news: New protections added to Kinetics KARE Foundation
We have big news for Kinetics customers on our “KARE Foundation” cyber plan. We've added new Browser Cyber-Protection We’ve found an amazing new security tool called ‘Conceal' that provides even more added protection. Cyber-security is all about layers and this one...
Penetration Testing
Penetration testing is important for businesses because it helps them identify and fix security vulnerabilities before they can be exploited by attackers. It can be a significant job as it needs a team of security professionals to simulate a real-world cyberattack....
What would you do?
Imagine – you are busily going about your day when suddenly your meeting is interrupted. “No one can access their files!!!” or “We just accidently paid $50,000 to a fraudulent account and we can’t get it reversed!!!” or something similar. What would you do? Where...
Security Updates
We need to make some security changes. These are in accordance with the continued work by Microsoft to protect 365 users. This will keep your configuration current with their latest advisories but may have some (limited) impact on your IT experience. It is all about...
Layered Security Works
There is no silver bullet in cyber-security. Best practice requires layers of protection. One of those layers is ‘geo-blocking’, which means you can only log in from specified countries and overcomes many of the African and Eastern European hacker fraternities....
Look out for LinkedIn Smart Links
This is a great example of needing new tools that didn't used to exist, to keep cyber-safe, even if they add cost to our cyber-protection. Hijacking your trust in LinkedIn Cybersecurity firm Cofense have detected phishing campaigns that used LinkedIn links called...