If you don’t where it is, you can’t protect it.
Do you know where ALL your organisation’s data is – not physically, but on which web and cloud services?
Here’s the problem. If you don’t where it is, then you can’t protect it. The secondary problem is finding out, because not everyone in your organisation will be onboard. It is common for people to sign up to web services because they offer something useful that helps them do their job.
They sign up using their email address and creating a password. There is the first headache – how does anyone track what has been signed up to across your organisation, let alone who has access to it? If that person leaves, no one will change the account credentials if they don’t know about it, but your ex-colleague still has access.
Secondly, what data do they upload? Is that data that you have a legal or moral responsibility for?
There’s nothing noble about Nobelium.
This isn’t theory – it’s real. USAID is a pretty important US organisation – promoting democracy and human rights around the world. Turns out, someone there was using a well-known email database tool called Constant Contact. But their account wasn’t well protected. Worse still, their account had a huge mailing set up, and of course, it had all the official USAID templates.
So, these Nobelium people, allegedly a Russian state-sponsored hacker group, compromised the Constant Contact account and sent a bulletin out. The bulletin contained malware that allowed the hackers to take command and control over victims computers. Ironically the fake email alleged interference in the US federal elections.

So, what can you do?
The first step is knowing what SaaS tools your people are using. We call this SHADOW IT and it is inevitable. Rather than stopping it, the job IT has is to identify it and manage it. The second step is to secure those platforms. That’s why our KARE for Security S2 plan contains a useful tool to help you identify what services your people are using.
Refer : What We Know About The Apparent Russian Hack Exploiting USAID : NPR
Would your cyber-security have saved you from this hack attempt?
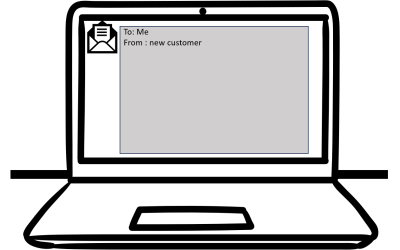
This is a real and very clever 'spear-phishing' attempt that one of our legal clients in Auckland received today.Would you have opened it? Would your IT have protected you?To: Me From : new customer Hello, My Husband and I are looking to buy a property (First-time...
Is it really you?
News that an elderly woman was tricked out of $100,000 over Facebook won't be a surprise to regular readers. She was fooled into thinking she was talking to a friend, and then sending money to access some make-believe Covid fund. AI makes it easy to speak in...
Ransomware claims increase 27%
The Coalition Insurance "2023 Cyber Claims Report: Mid-year Update" highlights the changing nature of the cyber threat landscape that businesses are currently facing, with a record surge in claims severity compared to the previous year. This is US data but it tends...
Webinar Replay : Learn How to Protect Yourself from the Darkweb Now
What does it mean If your personal details are leaked on the darkweb? Learn how you can manage your risks.The darkweb is a network of websites and servers that are not indexed by traditional search engines and require special software to access. It's a place where...
Protect Yourself from AI Phone Scams: A Terrifying New Trend
The rise of AI phone scams has brought personal targeting to a whole new level. Scammers are using AI-created fake texts (smishing) or even AI -created cloned voices of social media users. It has already found its way to New Zealand shores - New AI combats text...
KARE – Will your support plan need to change?
2008 was a long time ago. New Zealand was a different place. The IT maintenance needs of business were so much simpler! Locally, there was a change of government. Internationally, we were watching the start of the GFC with the fall of Lehman Bros bank. In the...
Putting a light on the dark web with upgraded monitoring
What's the Dark Web? The Dark Web, is often associated with a veil of notoriety, is a part of the internet intentionally hidden from traditional search engines. It requires specific software, such as Tor, to access, offering an anonymous platform where privacy is...
When does using CC in an email become a privacy breach?
Sometimes you need to use the BCC (Blind carbon copy) function in email! Last month, the email addresses of 147 gun owners were shared in an email. Whoever was sending the email put everyone in the 'cc' line. That meant their email addresses could be read by anyone...
Don’t accidentally throw away your WiFi!
Canon just sent out a warning. Wipe your old printers before selling/discarding them! It seems that printer technicians can access the memory and go into settings to uncover old Wifi passwords. Their advisory seems to suggest wiping the settings a couple of times...
Avoiding Subscription Bombs
If 10,000 emails suddenly flooded your inbox, what would you do? Suddenly any real messages will be lost in the blitz of spam that's overloading your screen. It is hard enough to delete all those messages, let alone filter out the genuine ones from the flood. This...