You are most vulnerable when you are busy, frantically jumping from call to call, meeting to meeting, distraction to distraction. So when you get a dodgy email, it’s very easy to open it.
This morning, that was me! And, even as hyper-aware as I am, I still *nearly* clicked on it.
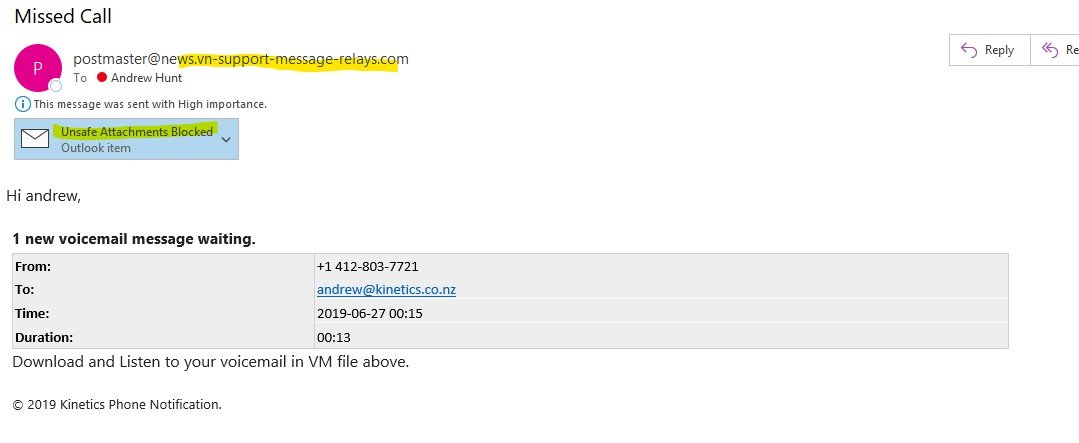
Thankfully (or rather – thanks to Microsoft ATP) , the message ‘unsafe attachments blocked’ was a good warning.
Then of course, a closer inspection tells the story – firstly, our voice messages look very different to this, AND we haven’t changed the system lately, and thirdly, that email address is really suspect.
The point is, even though those clues are VERY obvious, the busier you are, the more vulnerable you are. The more layers of security we can add, the more risk we can reduce (but alas, never eliminate)
Then I received this little beauty … its just the ‘admin-alerts’ in the email source that stands out – everything else looks legitimate.
If you then follow the link, say to look at the quarantine page (which, by the way, is spelt incorrectly in the email), it takes you to a page that looks legitimate, where you would enter your login details to access the logs – which almost seems sensible, except again the URL of the page is clearly false.
Very sneaky and almost looks legitimate. You have to be so careful.
However, using a tool like “message header analyser”, you can quickly see there is nothing legitimate about it.
Please be on your guard!



