Faced with a legacy practice management system coming towards end of support, Auckland city firm TBB tested the market and decided on partnering with Kinetics for the delivery of a replacement. Through the engagement, Kinetics has not only successfully migrated TBB to...
Kinetics News
REWATCH Did you know that, on average, 1.2 million Microsoft accounts get compromised every month?
Did you know that, on average, 1.2 million Microsoft accounts get compromised every month? According to Microsoft, 99.9% of hacked accounts didn't use MFA, and only 11% of all accounts have MFA enabled. The average cost of a ransomware security breach is $4.62...
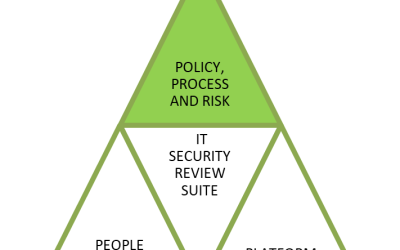
What level of cyber-security is right for my organisation?
The world is changing. Your company's cyber security is increasingly under threat and the costs of mitigation are often unwelcome. The first question organisations need to ask is whether they are exposed, and to what level. All the available data from sources like...
How many of these 10 layers of cyber protection do you use?
"A cybercriminal only has to be lucky once, while a defender has to be lucky every minute of every day.” - Combating Ransomware - A Comprehensive Framework for Action: Key Recommendations from the Ransomware Task Force. The message we hear from governance boards over...
How one business saved tens of thousands of dollars and lifted their customer experience with Microsoft 365
Haider and Ben are part of our 'Kambium' consulting division They specialise in helping organisations maximise their use of Microsoft 365 to achieve great efficiency. Ben & Haider can be contacted-:Haider.Khan@Kambium.co.nzBen.Fish@Kambium.co.nz Or click below to...
Opinion: Does ChatGPT make you safer?
Skynet who? There’s no end of sci-fi movies about the end of the world being brought on by self-aware AI tools. You can relax for now. ChatGPT is no such monster, but it does have an impact on our cyber-resilience. We’re watching universities and other educators...
The scammers are closing in on us.
Hacks don’t just happen to other people. The hackers are targeting all of us, every day. Every day, we have to defend them successfully. They only have to be successful onceWe all read about stories in the newspaper and there might be a sense of smugness that we...
What do YOU need to know about Juice Jacking?
You might get more than you bargained for. That sense of relief when you see a public USB charging point might be misplaced. There are increasing numbers of public USB charging points around. From aircraft and buses to fast-food restaurants, cafes, shopping malls and...
Is your licensing legit? Don’t be scammed
Don't get fooled! One of the great advantages of subscription software is that the licensing is easier to verify. The days of people copying license codes are over. That makes this scam even more interesting, simply because the product they refer to is subscription...
Webinar Replay : Updating what is ‘reasonable’ to protect your organisation from cyber-crime.
Cyber-security gets harder, so we make it easier. Much as the heading may sound 'double-dutch', it isn't. Simply, the levels of protection that are 'reasonable' to protect your organisation have changed. We need to do more, and at Kinetics we know that...